Bro Network Security Monitor Review

Information security has traditionally been divided into many different focus areas but i tend to lean most towards the way the united states department of defense us dod categorizes the domains of computer network defense cnd per dod 8500 2.
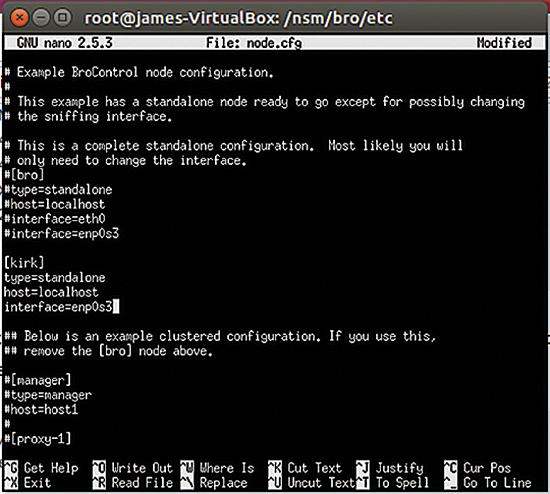
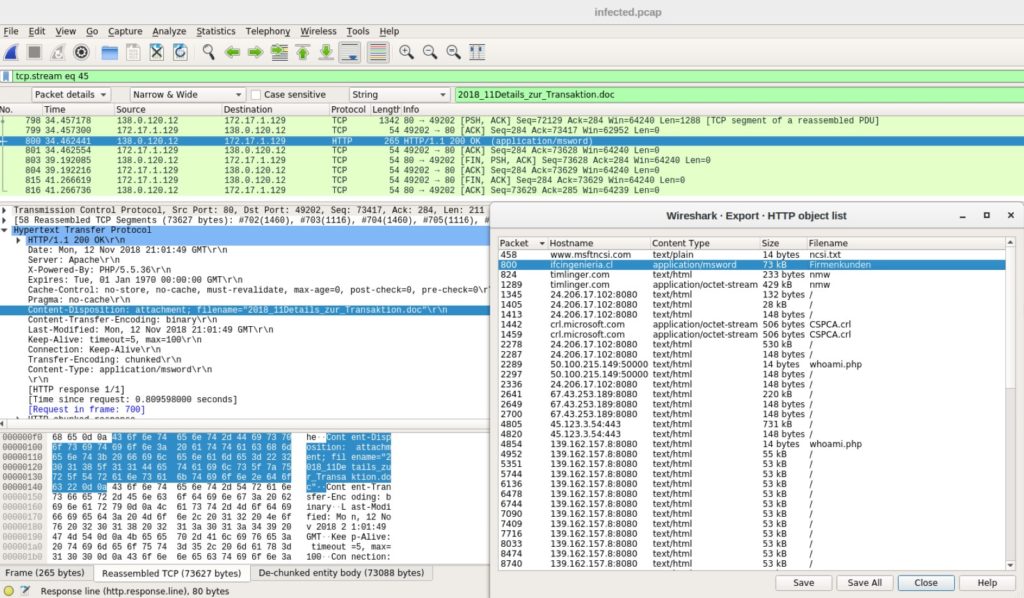
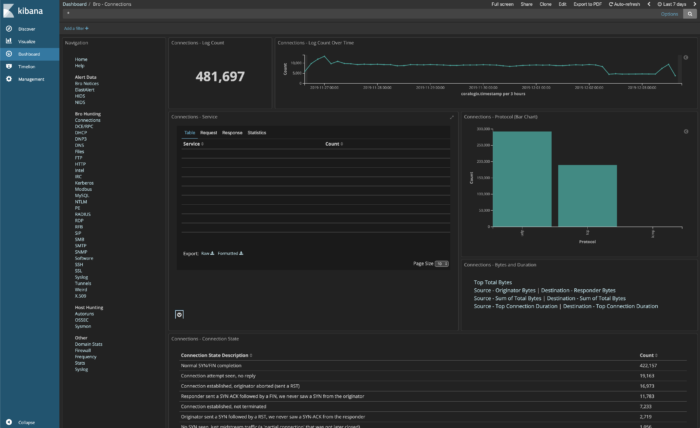
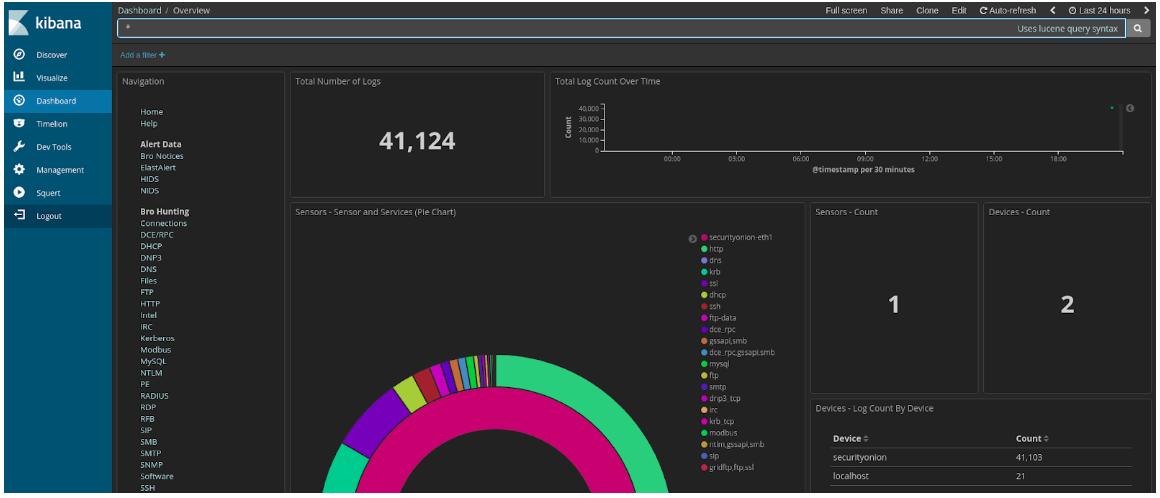
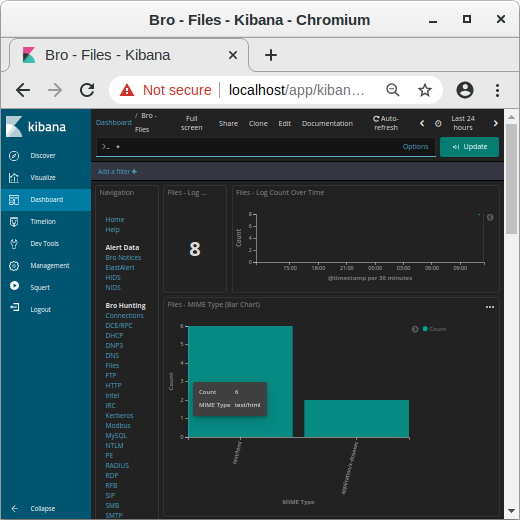
Bro network security monitor review. Bro network security monitor bro is a network intrusion detection system nids that passively monitors network traffic and looks for suspicious activity. This makes bro a very good intrusion detection system ids and network analysis framework. However the product camera pull down list default settings obviously do not follow ip camera manufacturer password acceptance criteria for instance with some foscam cameras acceptable passwords include any combination of letters numbers and some special characters however the security monitor pro v5 48 program. The product works very good so long as one knows the absolutes of networking.
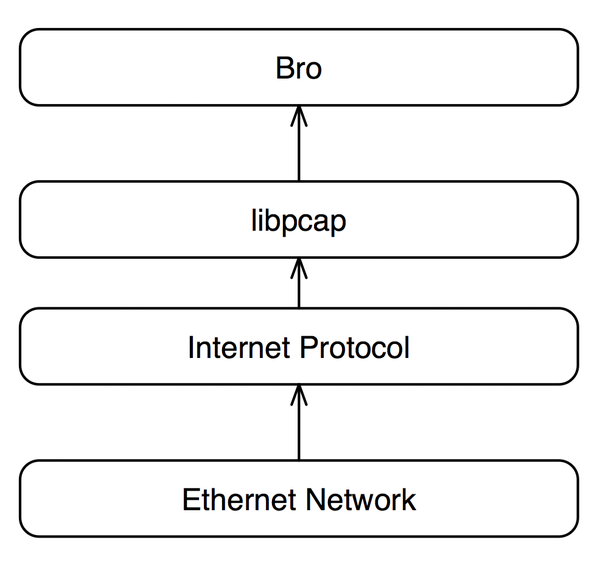
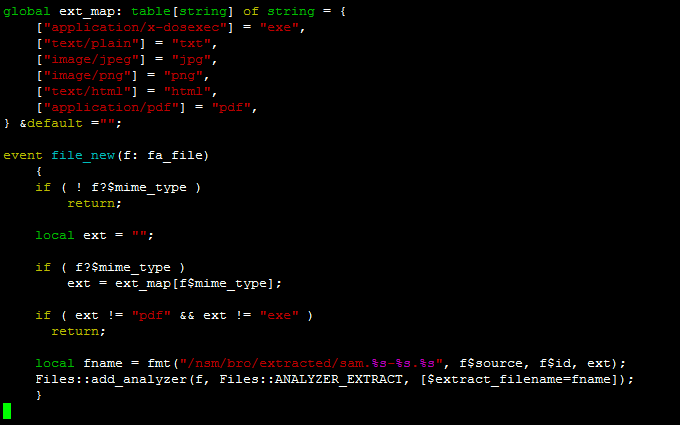
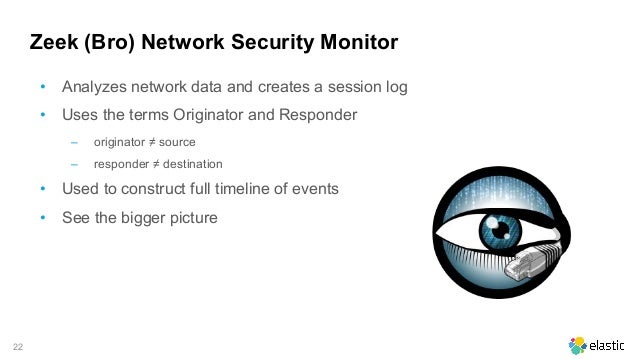
Bro detects intrusions by first parsing network traffic to extract is application level semantics and then executing event oriented analyzers that compare the activity with patterns. Zeek has a long history in the open source and digital security worlds. Chris sanders in applied network security monitoring 2014. The bro network security monitor bro is a network based analysis framework.
A free powerful way to monitor networks detect threats bro may have a new name zeek but the platform has the same rich functionality for security professionals. Those who know security use zeek.